EDF Luminus - Identity & Access Management StudyDecember 2017 till Feb 2018Content: |
 |
Management Summary
Security plays an important part in any organization. The enforcement of a security policy is not only to shield yourself from the outside world, but also to properly manage those stakeholders (employees, partners, customers...) who do have a right to perform certain actions, or to access certain information. We need to ensure a proper balance between restricting data from widespread distribution and making certain that business continuity is not compromised by security measures that are too restrictive. Any approach that creates this balance generates an added value to the organization.
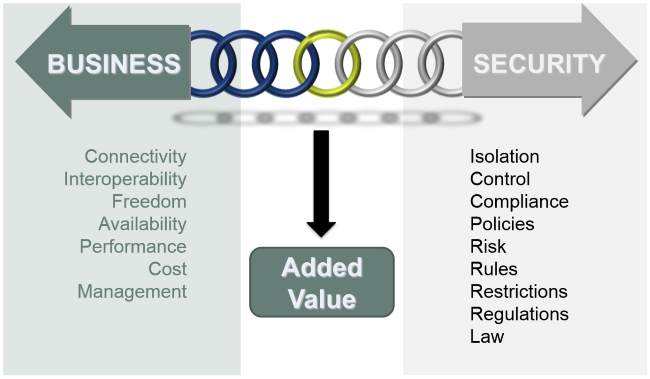
The main capability in such an endeavor is proper Identity & Access Management (IAM). This discipline has many different wording for the definition from many different sources, but the main idea of what it should be, surfaces in each of them:
The study is used as preparation for a future RFP, and has to generate insights on several requirements which the future structure of EDF Luminus will have, such as tooling, federation, delegation, possibilities for Software-as-a-Service (or rather Security-as-a-Service), Single Sign On, password policies, audit trails, control mechanisms…
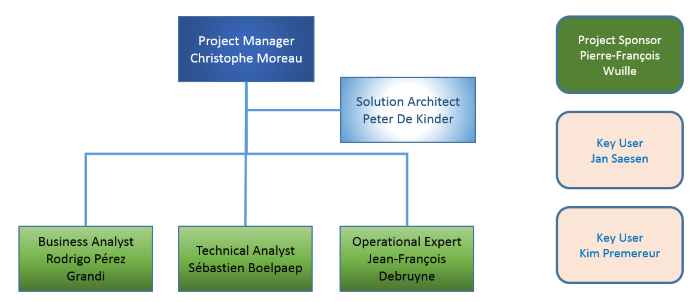
Team Composition
Lessons Learned
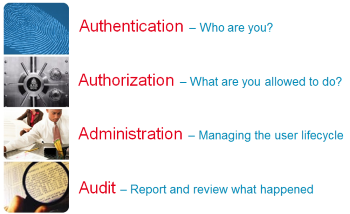
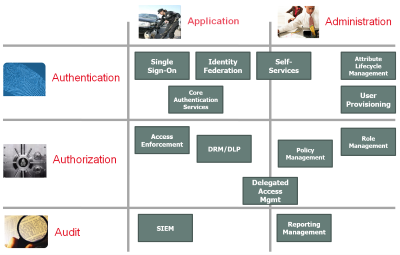
IAM as a discipline needs to address 4 pertinent points in order to cover the complete scope of needs. There can even be added an additional A with Application (as in the application of security) in contrast with Administration. When we map the core capabilities onto these 5 topics, we get the matrix as seen on the right hand side.
 |
 |
| Assessment | Security | Utilities Sector |


